Feb 8, 2019 16:50 UTC
| Updated:
Feb 8, 2019 at 16:50 UTC
Ring Signatures
With a frequent emphasis on privacy by users, significant development in technology has allowed for an impressive level of digital anonymity in value exchange.
Notably, a decisive technology known as Ring Signatures has been implemented in several privacy-centric cryptocurrencies, mainly the CryptoNote coins, which have emerged as the leaders in the user privacy realm.
Ring Signatures Background

Ring signatures are a sort of cryptographic digital signature and were actually invented back in 2001 by Adi Shamir, Ron Rivest, and Yael Tauman and subsequently introduced at Asiacrypt.
This concept is quite similar to that of group signatures, though, there is no way to identify the actual signer of a ring signature transaction and an arbitrary group of users can be incorporated in the ring signature without any additional setup.
The original concept was for ring signatures for functioning as an approach to leak secret information, particularly from high ranking government officials, without revealing who signed the message.
Since the original paper proposing ring signatures, there has been various optimizations and added features to the technology.
You May Also Read: What is MoneroV (XMV) Cryptocurrency?
How Do Ring Signatures Work?
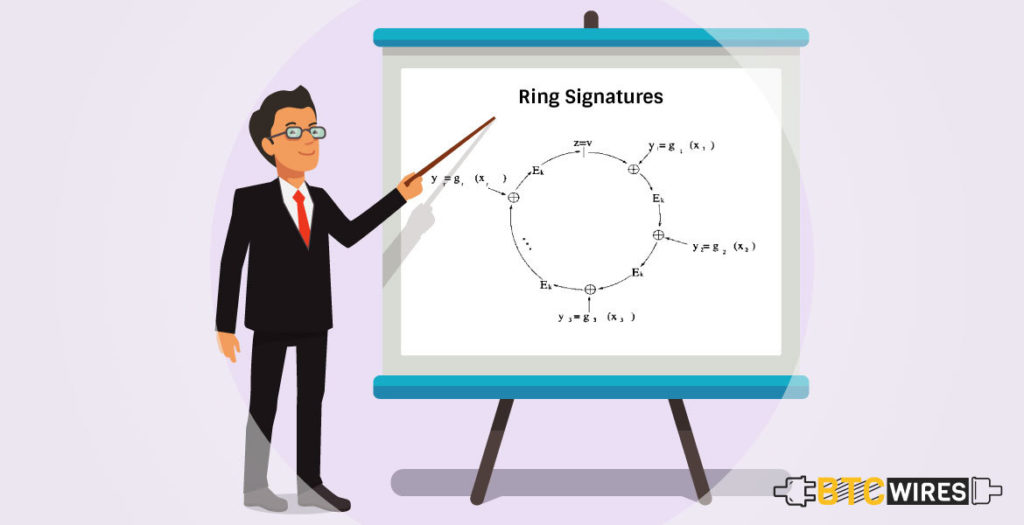
As mentioned previously, ring signatures are a cryptographic digital signature which is similar to a group signature.
However, ring signatures take the idea of group signatures further to offer even better privacy for the user.
In a P2P transaction format as is the case with cryptocurrencies, particularly using the CryptoNote coins as a reference, ring signatures protect the sender by obscuring the input side of a transaction, so it’s infeasible computationally to determine who the actual signer of a transaction is.
Ring signatures are a more sophisticated scheme than typical virtual signatures used in other digital currencies like ECDSA or Schnorr signatures.
Ring signatures may require multiple different public keys for verification, and the word “ring” is used because it consists of a group of partial digital signatures from various users that come together to form a special kind of signature used to sign a transaction.
This group is known as the ring and can be chosen arbitrarily from outputs from other users on the blockchain technology.
Ring signatures, conceptually, are akin to multiple parties signing a check from a joint bank account, but with a few implemented cryptographic approaches, whereby the actual signer isn’t distinguishable among the group.
The structure of a ring signature, using Monero as an instance, basically works as follows –
- Bob wants to send 10 Monero so he initiates a transaction through his Monero wallet to Alice.
- Bob’s digital signature for this transaction is a one-time spend key that starts with an output being spent from his wallet.
- The non-signers of the ring signature are past transaction outputs which are arbitrarily chosen from the blockchain and act as decoys in the transaction.
- All ring members are plausible signers of the transaction and it’s computationally infeasible for a 3rd party to detect the actual signer.
- All of the outputs of the ring signature together create the input of the transaction.
- The creator of the transaction (Bob) is provably eligible to spend the mentioned transaction amount without distinguishing his identity from the others in the ring.
- Though Bob’s public key is used in his own transaction, it might be used arbitrarily in other transaction in the Monero network as a muddling factor.
Moreover, the automatic creation of unique one-time keys prevents transaction linkability and is made possible via an optimization of the Diffie-Hellman key exchange.
An issue that you may notice with having anonymous transactions across a privacy-centered cryptocurrency network like Monero is that prevention of double-spending, that we noticed in bitcoin double spending, protection was not guaranteed.
This is cleverly solved with the use of key images in conjunction with the ring signature scheme.
A key image is a cryptographic key derived from an output being spent and is part of every ring signature transaction.
There is just one unique key image for each output on the blockchain and and a list of all used key images is maintained on the blockchain.
Owing to the cryptography key images, it’s impossible to make a correlation between an output on the blockchain as well as its key image.
As the CryptoNote website puts it “All things considered, the key image is unavoidable, unambiguous, and yet an anonymous marker of the private key” used in a transaction.
Any new ring signature that use a counterfeit key image are automatically rejected as being an attempted double-spend.
You May Also Read: Cryptocurrency Halving
Ring Signatures Usage
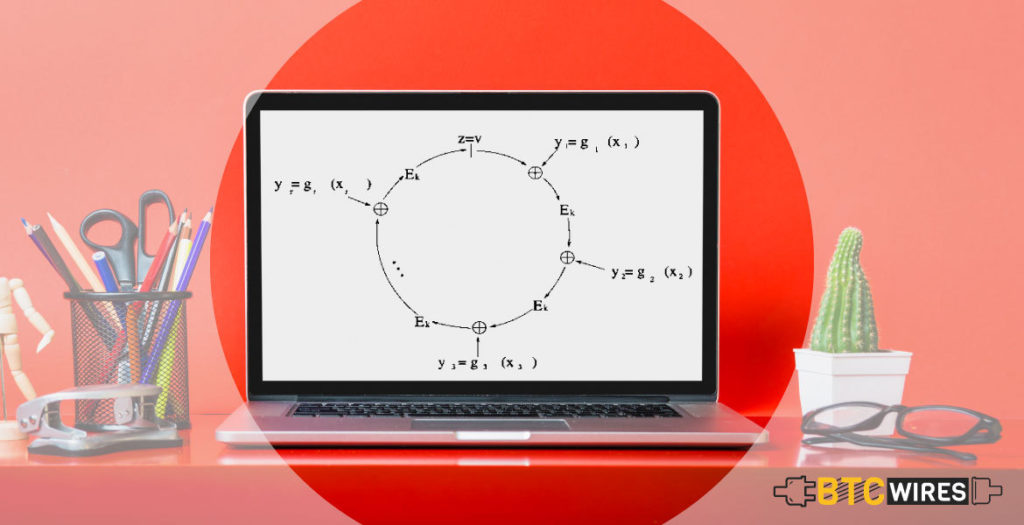
Ring signatures are a vital component of many privacy-centered cryptocurrencies and need to be more relevant moving forward as a kind of standard implementation for digital signature schemes at a degree of anonymity which is looking to be achieved for the user.
The CryptoNote coin are the most well-recognized privacy-centered coins that provide ring signatures and Ring CTs.
Some of the more prominent CryptoNote coins incorporate and Bytecoin, with Bytecoin being the first CryptoNote-based currency.
Discussions surrounding the implementation of ring signatures as well as other privacy preserving methods, which have arisen as a result of recent innovations in technology, have been floated for various legacy digital currencies which are looking to offer better privacy for their users.
You May Also Read: IOTA: The Future Cryptocurrency of IoT?
Final Thoughts
There are many components which go into creating as well as maintaining a cryptocurrency network that offers user anonymity.
Ring signatures as well as their subsequent optimization with Ring CTs are crucial to obscuring sender identities as well as transacted amounts across a network.
More emphasis will lead to to privacy as mainstream adoption of cryptocurrencies moves forward. With novel technologies being innovated at an accelerated pace, it will be enthralling to watch the continued development and ultimate end results of these privacy-focused networks.
Here are a Few Articles for you to Read Next:


























































